TAMPA, Fla. — A Tampa-based company recently had to implement new measures to secure their computer systems after they fell prey to a hacker's phishing scheme. Cybersecurity experts say the case is just part of a growing trend.
- Hackers now targeting small and mid-size companies
- Phishing schemes target sensitive financial information such as bank account numbers
- More Hillsborough County stories
Clients and colleagues of Tampa-based Omni Public received an email claiming its Managing Director, Cesar Hernandez, had confidential information to share.
But there was a problem: Hernandez never sent it.
“I started noticing suspicious activity in my email and people calling me, ‘Hey, you just sent me this document for review’ and I'm like, 'I didn't send anything,'” said Hernandez.
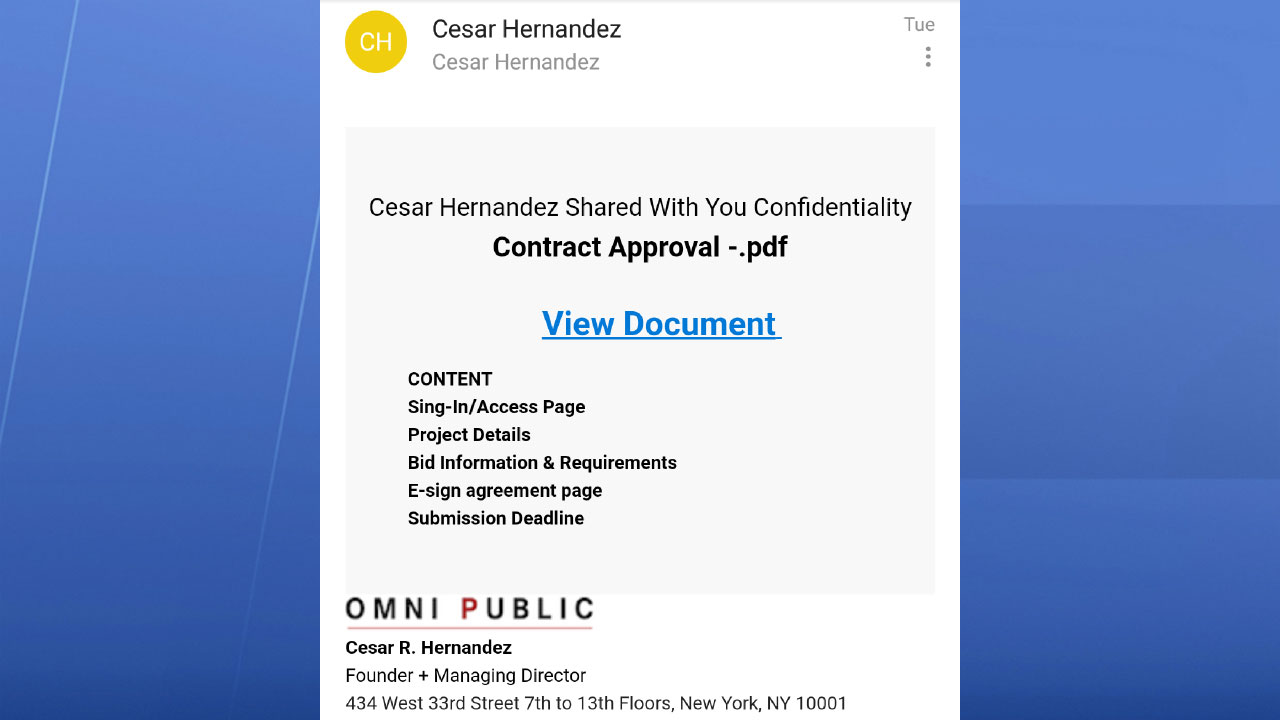
This screen capture shows the phishing email employees and clients of Omni Public in Tampa received. (Courtesy: Cesar Hernandez)
He soon realized he and his company were victims of a phishing scheme, where hackers attempt to get sensitive financial information like banking account numbers by sending out false emails.
After contacting the FBI's cybercrimes unit, Hernandez went to work on securing what could.
“I had to suspend my emails, reroute all my accounts and get a VPN (virtual private network),” he said. “I had to put in all these systems in place to make sure my system was ok.”
Cybersecurity expert Vikas Bhatia says hackers are now aggressively targeting smaller and mid-sized companies over larger corporate conglomerates.
“They’ve realized it’s easier to break into and exploit the smaller organizations than the larger organizations,” said Bhatia, CEO of Just Protect, a cyber security firm.
Bhatia, who has worked in cyber security for 20 years, recommends changing passwords, using the most current updates for software and hardware and having a two-step verification process in place to avoid becoming a victim’s of cyber hackers.
“If you do the basics, then you're alleviating 80 to 90 percent of the problems that the hackers and the bad guys end up actually exploiting,” he said.



